Administrators with HPE servers in their environments are being warned that a rootkit is circulating that takes advantage of a vulnerability in the Integrated Lights Out (iLO) management utility to wipe hard drives.
It can’t be removed by firmware upgrades and can be hidden for a long time, says a report by an Iranian-based application vendor called Amnpardaz Soft Co.
Dubbed iLOBleed, the malware has been used by hackers “for some time,” says the report. The rootkit adds a malicious module researchers call Implant.ARM.iLOBleed.a to the iLO firmware and modifies a number of original firmware modules. The rootkit silently prevents firmware updates while pretending to complete them. It also provides access to the server hardware, which can allow an attacker to completely wipe server disks.
iLO enables admins to remotely configure, monitor, and update many ProLiant servers seamlessly, from anywhere in the world. Upgraded licences add a graphical remote console, multi-user collaboration, video record/playback, remote management and more.
The researchers’ report notes iLO has full access to all the firmware, hardware, software, and operating systems installed on the server. As a result, they say iLO is an “ideal utopia for malware and APT groups” because of the high privileges an approved user can get, and “the general lack of knowledge and tools for inspecting iLO and/or protecting it.” In addition, iLO is always running.
Accessing and infecting iLO is not only possible through the iLO network port, but also through system administrator or root access to the main operating system, the report says. This means that if an intruder has access to a user ID with administrator/root privileges for the main operating system installed on the server, it can – without needing any further authentication – directly communicate with the iLO, and infect it if it is vulnerable.
The report says the biggest risk is to iLO4 and its earlier versions used on HP G9 and below servers. That’s because there is no Secure-Boot mechanism with an embedded Trusted Root Key in the hardware, so the firmware of these versions is more likely to be modified and infected by malware.
However, researchers add, even if iLO has been updated to the latest version that does not have any known vulnerabilities, it could still be downgraded to a lower version, which makes infecting fully-patched firmware possible. This can be prevented in G10 series servers if a non-default setting is enabled. On earlier servers, it is not possible to prevent the downgrade mechanism.
Totally disconnecting the iLO network cable or upgrading firmware to the latest version isn’t enough to prevent malware infection, the report adds.
On the bright side, there is a relatively simple way of detecting a compromise: When the malware silently blocks a legitimate iLO firmware upgrade process, it displays a fake “upgraded” version in the web UI. However, HPE has changed the UI of the iLO considerably, as seen below.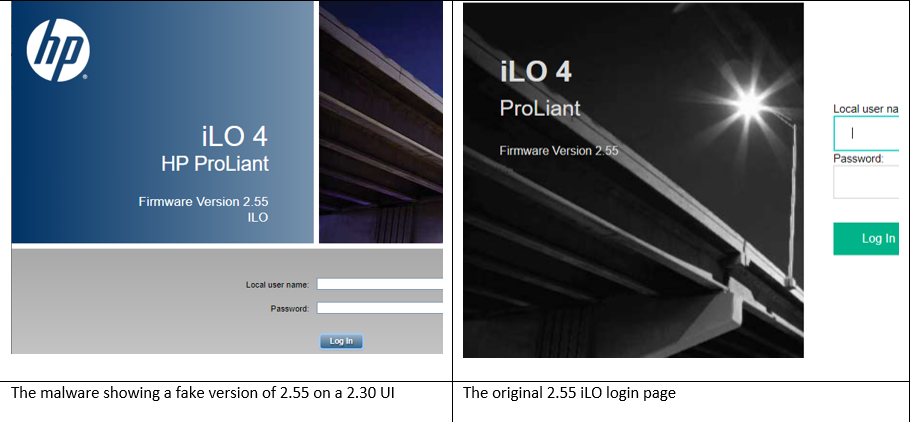
However, the threat actors behind this malware will likely catch on fast and change the graphic.
Unlike other “wiper” malware, says the report, this is not a one-time hit-and-run disposable attack. It is designed to stay under the radar for extended periods by preventing an iLO firmware upgrade; even the exact version number of the current firmware is extracted and displayed in appropriate places in the web console and other locations.
“This alone shows that the purpose of this malware is to be a rootkit with maximum stealth and to hide from all security inspections,” says the report. “A malware that, by hiding in one of the most powerful processing resources (which is always on), is able to execute any commands received from an attacker, without ever being detected.”
For defence the researchers recommend IT teams
- not connect the iLO network interface to the operating network and improvise a completely separate network;
- periodically update the iLO firmware version to the latest official release from HPE;
- configure iLO security settings on HP/HPE servers, and disable downgrade for G10 servers;
- use defense-in-depth strategies to reduce risk and detect intrusions before reaching the iLO;
- and periodically use the iLO Scanner tool to detect potential vulnerabilities, malware, and backdoors in the current version of the iLO Server firmware.
