One of the latest bank phishing campaigns aimed at Californians has a Canadian twist: The targets are supposed to be customers of the Royal Bank.
Trend Micro said Tuesday in a blog it detected three waves of phishing email totaling 13,000 messages between July 22 and Aug. 8 apparently aimed at Californians who attackers hope are clients of Royal Bank of Canada. Recipients are addressed as “Dear RBC Express customer” plus a name. The message then claims user roles have been updated and asks the recipient to click on an attachment to approve.
Separately, Canadian banks have been alerted to a possible imminent global ATM attack (see below).
The phishing email comes with an HTML file that takes the victim to an exact copy of an RBC site, where their login credentials would be stolen:
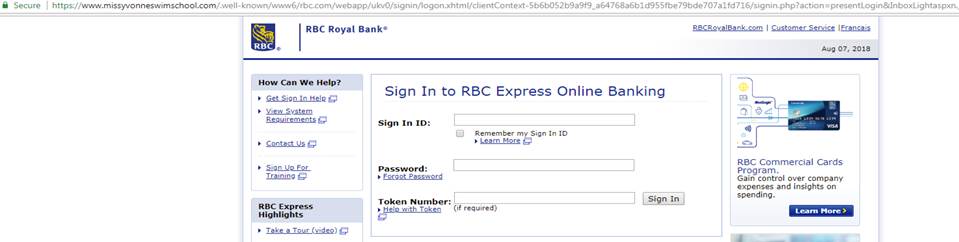
While the attachment has highly obfuscated Javascript in an attempt to make discovering its malicious URL more difficult, there are a number of clues that this message isn’t legit. First, if the example posted by Trend Micro is typical, the sender’s email address bears no evidence it comes from the bank. (In this case it’s “sale@bonsaistore.ca”). Second, the language of the message is stilted, third the attachment has a scrambled file name and fourth, even if the victim goes to the malicious web page, the page’s URL has nothing to do with the bank (in this case it’s “www.missyvonneswimschool.com.”)
That’s assuming a victim notices these things. Trend Micro says usually about four per cent of targets will fall for a phishing scheme.
Greg Young, the vendor’s vice-president of security, said in email the campaigns were broadly based and the targets weren’t necessarily RBC customers.
At press time an RBC spokesperson had not replied to a request for comment.
It isn’t clear how many U.S.-based RBC Express customers there are. RBC has had operations south of the border for decades, including opening an office in Los Angeles in 1961. In 1989 it stopped offering retail banking in the U.S., preferring to concentrate on business banking until 1998 when it bought online bank Security First Network Bank. It later bought Centura Banks and expanded into Florida, Alabama, Georgia and Texas. Then, after being caught in the U.S. financial housing crisis, RBC Bank USA was sold in 2011. RBC said it then restructured its U.S. banking operations to focus on the personal banking needs of Canadian cross-border clients and U.S. clients of its personal wealth management service. In 2015 it returned to offering retail banking services to American customers by buying Los Angeles-based City National Bank.
It isn’t common for the foreign operations or customers of a bank to be targeted by hackers — usually they go after any customer of a financial institution — although they might not have realized RBC Bank is headquartered outside the U.S. One reason might be the attackers have a stolen list of California-based RBC customers and their email addresses. “Normally these campaigns wouldn’t be geographically centered like this,” said Young.
That’s one of the unique elements of this campaign. Another is the use of an HTML attachment and the third is the quality of the phony login page.
Canadian banks aren’t immune to phishing scams. According to spamfighter.com, in 2011 security vendor GFI Labs spotted fraudulent security update messages being sent to RBC customers.
Experts say security awareness education for consumers is the best way to stop from being stung by such a campaign.
(Editor’s note: This story has been updated from the original, which said it wasn’t clear if all the targets of the email were in fact RBC customers)
ATM attack warning
Meanwhile security reporter Brian Krebs said on the weekend that the FBI has quietly alerted banks that criminals are preparing to carry out a highly choreographed, global fraud scheme known as an “ATM cash-out,” in which crooks hack a bank or payment card processor and use cloned cards at cash machines around the world to fraudulently withdraw millions of dollars in just a few hours.
UPDATE: India’s Cosmos Bank, based in the western city of Pune, said hackers used malware last weekend to steal customer information from the company’s ATM server, then used that data to clone thousands of Visa and RuPay debit cards and steal the equivalent of US $13.5 million. The debit cards were then used over the weekend in a number of countries including Canada, Hong Kong, and India.
In an interview Aaron Boles, vice-president of communications at the Canadian Bankers Association, said it has also been alerted through the financial industry who relayed the message to member banks. A typical police or intelligence warning wouldn’t have attack details, he said. Instead banks would be told to be vigilant for threats and have all software patched.
Compromising an ATM for big bucks is increasing. In January Europol announced eight people in Romania and Moldova had been arrested following a number of ATM attacks in Europe. The gang allegedly pried open the machines and installed malware that let them empty the ATM of cash.
In 2016, Krebs says, ATMs of the National Bank of Blacksburg, Virginia were emptied of U.S. $2.4 million from customer accounts. According to the New York Times, in 2012 a gang stole US$45 million from thousands of ATMs in 20 countries in a few hours. According to an indictment, it started when hackers infiltrated the system of an unnamed credit-card processing company in India that handles Visa and MasterCard prepaid debit cards. Then they raised the withdrawal limits on five prepaid MasterCard debit accounts issued by a bank in the United Arab Emirates. The debit cards for those five accounts were then cloned multiple times for the gang to use as often as they could.
Boles said while there have been successful individual ATM attacks in Canada where a card-capturing device was surreptitiously attached to a keypad, there hasn’t been a successful cashout strike of the type described by Krebs in the FBI warning. “We still see some (bank or credit card) skimming activity but the alerts are sporadic and localized in nature,” Boles said. Thanks to the introduction here of bank and credit cards with security chips, so far there’s no evidence of criminals being able to clone cards so they can steal cash. Bank and credit cards that are vulnerable to cloning only have magnetic strips on the back. These are still common in the U.S., although they are being replaced with chip and PIN cards.
Still, Boles said, the CBA urges people to cover a keypad when entering a PIN number in case a criminal has been able to install a pinhole camera to record what people punch in.
