The number of ransomware attacks around the world continues to increase, which isn’t surprising given how lucrative the technique can be. Here’s a summary of some of the most recent sightings:
—British-based security writer Graham Cluley reports today that a number of companies have received email threatening their sites with distributed denial of service (DDoS)a attacks if they don’t pay the equivalent of US$720 in Bitcoin by Sept. 30.
The mail comes with the topic header “DDoS warning” and the following message:
FORWARD THIS MAIL TO WHOEVER IS IMPORTANT IN YOUR COMPANY AND CAN MAKE DECISION!
We are Phantom Squad
Your network will be DDoS-ed starting Sept 30st 2017 if you don’t pay protection fee – 0.2 Bitcoin @ [removed].
If you don’t pay by Sept 30st 2017, attack will start, yours service going down permanently price to stop will increase to 20 BTC and will go up 10 BTC for every day of attack.
This is not a joke.
I’m reaching out to my Canadian contacts to see if the threat has been received here.
—Lawrence Abrams at Bleeping Computer reports that a researcher named Malware Blocker has discovered a new bootlocker ransomware, which has been dubbed RedBoot. The code will encrypt files on the computer, replace the master boot record of the system drive and then then modifies the partition table.
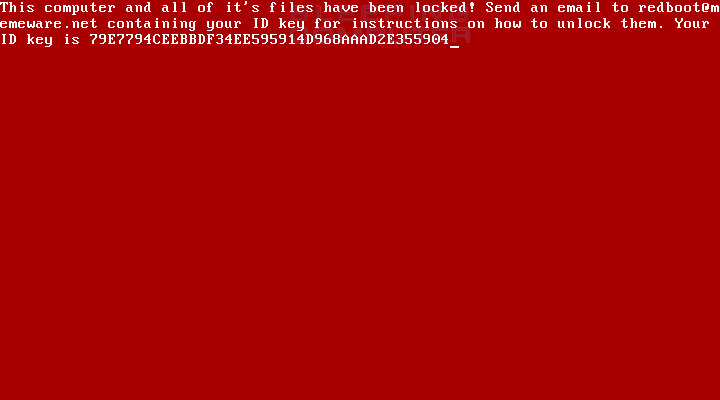
(Redboot screen. Source: Bleepingcomputer.com)
“As the ransomware does not provide a way to input a key to restore the MBR and partition table, unless the ransomware developer has a bootable decryptor this malware may be a wiper,” says the news report. That means paying the ransom and expecting a decryption key may be a waste of money.
When executed it extracts five other files into a random folder in the directory that the launcher was executed. These files are boot.asm, assembler.exe, main.exe (which encrypts the files), overwrite.exe (which overwrites the MBR), and protect.exe (which terminates and prevents various programs from running, including task manager and processhacker).
–Last week researchers at Carbon Black published a column noting that at the moment — and remember that caution — an analysis of a large set of ransomware families by the company suggests most attacks are simple in an effort to target a mass set of victims as easily and quickly as possible. Or as they put it, ” Attackers are looking to make quick, easy money with unsophisticated malware, combined with sophisticated delivery methods.”
However, the authors also note that the level of sophistication is increasing. For example, the WannaCry and NotPetya versions included worm functionality to spread across networks. And some ransomware is thought to really be a cover for nation-state backed attacks aimed at wiping data from victims’ machines.
The other interesting observation of the Carbon Black researchers is that “episodic ransomware attacks, such as NotPetya, have made for splashy headlines, but reveal more about the general unpreparedness of worldwide businesses to handle these attacks than they do about a sophisticated evolution of ransomware. These attacks highlight that the industry at large is often failing to do infosec basics, such as patching. Businesses appear to be focusing too greatly on next-generation threats while being unable to defend against the current era of basic malware.”
–Buttressing this is a column by Steve Ragan at CSO Online, who reports that at last week’s DerbyCon security conference in Louisville a network administrator at a small U.S. law firm talked about how he survived two ransomware attacks: Daily backups that are monitored and tested. There’s a daily, a weekly, a second daily that isn’t on a shared drive, and offsite backups. His other strategy is awareness training.
Note that this firm was stung by ransomware — in one case the malware came in an image, which a staffer was expecting to receive. By coincidence, apparently, the first name the attacker used in the message was the same as the one the staffer was expecting so the image was opened. However, the firm was able to recover by being prepared.
So while doing the basics — patching, backups and awareness training — are vital today, remember this from the Carbon Black researchers: As the sophistication of these attacks increases, security teams will have to implement better lines of defense to detect complex malware and adversaries using non-malware attacks to encrypt data.
