A recent survey by network equipment provider Cisco Systems Inc. indicates that Canada’s highly Web connected Generation Y workforce has a serious disconnect with corporate IT security policies.
Cisco surveyed 1,800 college students and workers aged 18 to 30 as well as 1,800 information technology professionals in 18 countries including Canada, the United States, Mexico, The United Kingdom, Russia, Korea, and Japan.

RELATED CONTENT
Gen Y: More tech savvy, less security conscious
Gen Y workers: We know all about this IT stuff
Gen Y to CIOs: What we expect from social media
When asked if it was all right for employers to track employees’ activities online if the workers are using company devices, 72 per cent of the Canadian respondents said no and only 28 per cent said it was okay.
Cisco’s surveyed also found what many parents of teenagers have known for the past five years. In Canada 92 per cent of so-called millennials feel the age of privacy is over with some 34 respondents saying they are not worried at all about data about them that is stored by online sites they visit. No less than 57 per cent of the Gen Y respondents said they were comfortable with their personal information being used by retailers, social media sites and other online sites if they benefit from the experience.
In the third quarter of 2012, FortiGuard Labs detected high activity levels of ZmEu, a tool that was developed by Romanian hackers to scan Web servers running vulnerable versions of the mySQL administration software (phpMyAdmin) in order to take control of those servers. Since September, the activity level has risen a full nine times before finally levelling off in December.
Lovet outline four methods commonly used by attackers:
1. Simda.B: A malware that poses as a Flash update in order to trick users
into granting their full installation rights. Once installed, the malware
steals the user’s passwords, allowing cybercriminals to infiltrate a victim’s email and
social networking accounts to spread spam or malware, access Web site admin
accounts for hosting malicious sites and siphoning money from online payment system
accounts.
2. FakeAlert.D: A fake antivirus malware that notifies users via a convincing-looking
pop-up window that their computer has been infected with viruses, and
that, for a fee, the fake antivirus software will remove the viruses from the victim’s
computer.
The infection either prevents a user’s machine from booting or encrypts data on the victim’s machine and
then demands payment for the key to decrypt it.
Zeus crime-kit. It intercepts a user’s online bank login attempts and then
uses social engineering to trick them into installing a mobile component of the malware
on their smartphones. Once the mobile element is in place, cybercriminals
can then intercept bank confirmation SMS messages and subsequently transfer funds to a
money mule’s account.

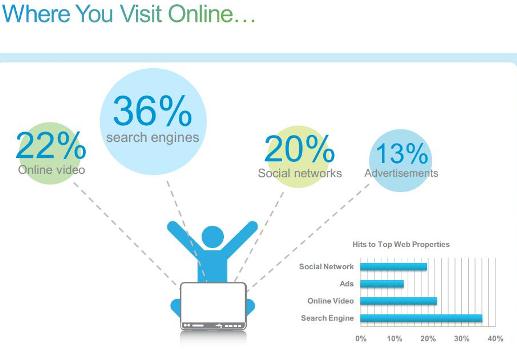
“Today, we live in a blended work-personal life,” according to John Stewart, senior vice president and chief security officer for Cisco’s Global Government and Corporate Security. “The hackers know this and the security threats that we encounter online such as embedded Web malware while visiting popular destinations like search engines, retailers and social media sites and smartphone tablet apps no longer threaten only the individual, there also threaten the organizations by default.”