Despite the growing number of mobile attacks, companies that were early in adopting the bring your own device trend are more likely to be in a better position to face mobile risks than firms who are late in the game, according to a report from security software provider Symantec Corp.
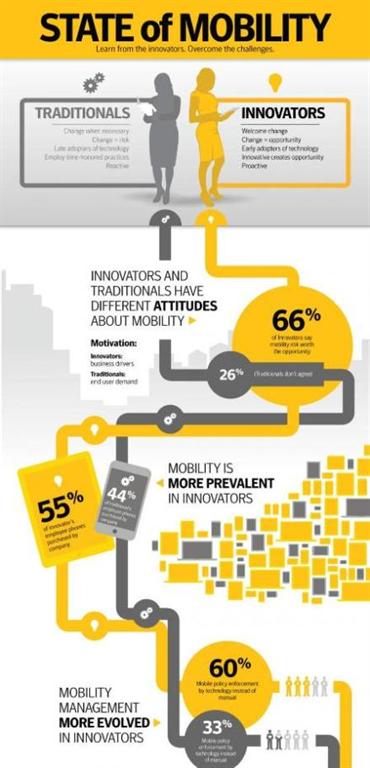
“These attitudes may be influenced by different risk perceptions,” the report said. “Two thirds of innovators feel that the benefits of mobility outweigh the risk, while three-quarters of traditionals feel that is not the case.”
There are 50 per cent more employees using smart phones in innovator companies compared to traditional firms. In addition, 83 per cent of innovators are also considering creating corporate app stores compared to only 55 per cent among traditionals.
As a result of their early exposure to BYOD and their realization of the benefits of mobility, innovator companies tend to have “more evolved” mobility management policies, according to Symantec.
For instance, more than 60 per cent of innovator firms have a mobile policy enforced by technology rather than one reliant on manual tools. By contrast, only 33 per cent of traditional firms use technology to enforce their mobile policies.
At least one security expert says technology-aided mobile policies have become a must for many large organizations.
RELATED CONTENT
Samsung goes after enterprise with enhanced MDM
Citrix creates MDM solutions
“I have great respect for and recognize the importance of security training for employees,” according to Claudiu Popa, principal of Informatica Corp., an international IT security consultancy firm based in Toronto. “However, manual processes can only go so far.”
He said, with large companies that may deploy hundreds if not thousands of different remote devices, employing technology to assist IT administrators in mobile device management (MDM) becomes imperative.
“You can always tell employees not to stay away from suspect Web sites,” he said. “The reality is if you give or allow an employee to take home a laptop, tablet of smart phone, they will likely use it to connect to the Internet and use if for something other than work.
Popa said, there are many MDM tools in the market today that allow administrators to monitor, track and control devices remotely. Such tools can be used to enforce policies by helping administrators configure devices to limit use and network access.