When IT administrators deploy Web gateways, firewalls, remote access servers and other security appliances, they expect these products to protect the corporate network from attacks, keep malware out and prevent data leaks.
However, a penetration tester for British information security company NCC Group said the very systems organizations deploy to protect their networks are likely to be riddled by vulnerabilities.
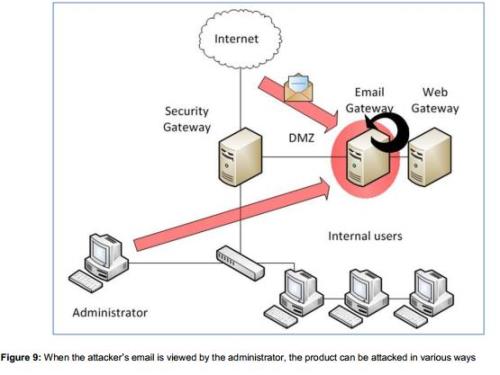
In his report titled Ironic Exploitation of Security Products which he presented onThursday at the Black Hat Europe 2013 security conference in Amsterdam, Williams said he found most security appliances were poorly maintained Linux systems saddled with insecure Web applications.
“There may be a temptation to think of security appliances as fortified; i.e. especially secured and hardened, or that these devices have undergone thorough and comprehensive security testing to eliminate insecurities as part of a secure development lifecycle,” Williams wrote. “This research shows that this appears to be mostly not the case, and rather basic and easily identified and common security issues were discovered in almost all security appliances tested.”
Among the appliances he tested were products from prominent vendors such as Barracuda, Cisco, Citrix, McAfee, Sophos, Symantec and Trend Micro.
William’s research involved investigated the products’ Web user interfaces, and other potential attack vectors such as firewalls, multifunction gateways, antispam and antivirus filters for email and remote access gateways.
He often employed direct attacks in cases where access to the UI or other protocols was exposed. Some of the attacks were performed by external attackers employing “a small amount of reconnaissance and social engineering” and going through internal users and It administrators.
Many of the vulnerabilities Williams found resided in the Web-based UI of the products.
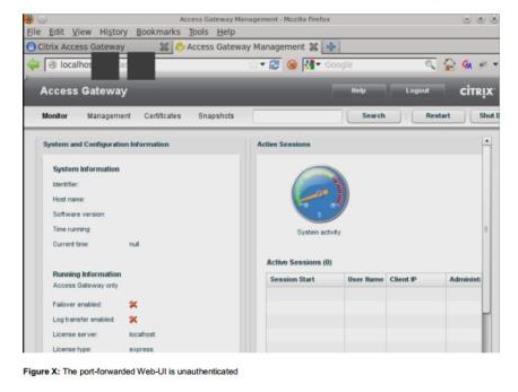
Many of the units also showed information about product model and version numbers which could be used by attackers to determine vulnerable appliances.
A number of the interfaces also had flaws that would allow command injection and privilege escalation.
“The most surprising finding was that various IT vendors do not appear to follow secure development lifecycles to minimize the likelihood of these common classes of issues appearing in their products,” Williams said in his report. “…a small number of vendors seemed unable to understand the significance of some issues or to produce fixes in a reasonable timeframe.”
He said some vendors dealt with the issues within three months while others have not even addressed similar issues after nearly a year.
Read the rest of Ben Williams’ report here