While direct attacks on enterprise networks through phishing and SQL injection are common, threat actors are also looking for weaknesses to exploit in any software even before it gets to organizations.
That’s illustrated in two news stories this week, one about a backdoor it dubs “ShadowPad” and planted in a server management software product used by hundreds of large businesses worldwide, the other about the hacking of developers of Chrome extensions to distribute spam to unsuspecting users.
Kaspersky Lab researchers reported discovering the backdoor had been planted in software builds released last month from NetSarang Computer, which makes a range of network management and connectivity solutions including Xmanger Enterprise. The backdoor allows attackers to download further malicious modules or steal data. Kaspersky determined the malicious module has been activated at least once, in Hong Kong,
NetSarang has been notified and issued a fix. Anti-virus companies have also been notified and AV products may by now detect the malware. Affected products are
- Xmanager Enterprise 5.0 Build 1232
- Xmanager 5.0 Build 1045
- Xshell 5.0 Build 1322
- Xftp 5.0 Build 1218
- Xlpd 5.0 Build 1220

(Kaspersky screen shot of Backdoored dll in a list of loaded modules of Xshell5 software)
Kaspersky said it learned about the problem after being approached by one of its partners, a financial institution, about about suspicious DNS (domain name server) requests originating on a system involved in the processing of financial transactions. The source was tracked to NetSarang server management software.
The malicious module would start sending DNS-queries to command and control server once every eight hours. The request would contain basic information about the victim’s system (user name, domain name, host name). Kaspersky believes if the attackers considered the system to be “interesting,” the command server would reply and activate a fully-fledged backdoor platform that would silently deploy itself inside the attacked computer. After that, on command from the attackers, the backdoor platform would be able to download and execute further malicious code.
In a statement NetSarang said that to combat cyberattacks it has incorporated measures to prevent its products from being compromised. “Regretfully, the Build release of our full line of products on July 18, 2017 was unknowingly shipped with a backdoor, which had the potential to be exploited by its creator. The security of our customers and user base is our highest priority and ultimately, our responsibility. The fact that malicious groups and entities are utilizing commercial and legitimate software for illicit gain is an ever-growing concern and one that NetSarang, as well as others in the computer software industry, is taking very seriously.”
As a result of the incident it has added “a more robust system to ensure that never again will a compromised product be delivered to its users.”
Lessons to infosec pros: Always be on the lookout for suspicious network activity, and be on the lookout for product updates from third party suppliers.
The increased hijacking of Chrome extensions is a warning to infosec pros to limit their use by end users for all browsers. While extensions may be appreciated for bringing some productivity gains to users, the risks may outweigh the benefits.
Security vendor Proofpoint outlined the discovery in a blog which said that the end of July and beginning of August, several Chrome extensions were compromised after their author’s Google Account credentials were stolen through phishing. While it resulted in the hijacking of traffic the also exposed users to potentially malicious popups and credential theft.
Those apps modified include Web Developer 0.4.9, Chrometana 1.1.3, Infinity New Tab 3.12.3,, CopyFish, Web Paint 1.2.1, and Social Fixer 20.1.1. Proofpoint also suspects two VPNs were also compromised in June. Proofpoint suspects one threat actor was behind it all.
The compromised version of the extension attempts to substitute ads on the victim’s browser, hijacking traffic from legitimate advertising networks, says Proofpoint. But in many cases, victims were presented with fake JavaScript alerts prompting them to “repair” their PC then redirecting them to affiliate programs from which the threat actors could profit.
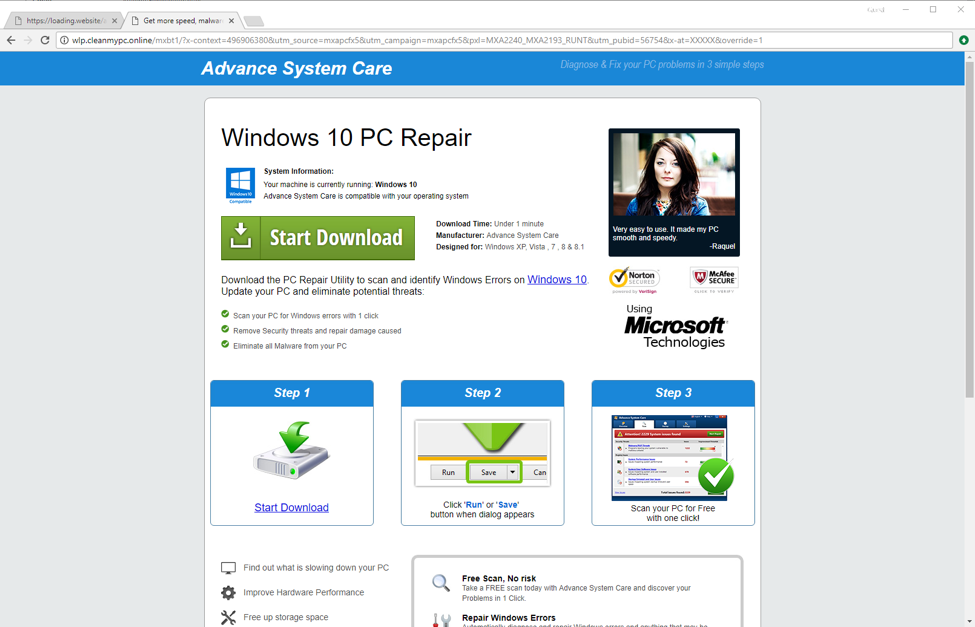
(Proofpoint screen shot of a fake PC repair website)
“Threat actors continue to look for new ways to drive traffic to affiliate programs and effectively surface malicious advertisements to users,” concludes Proofpoint. In gaining developer credentials through emailed phishing campaigns, attackers can publish malicious versions of legitimate extensions and gathering and exfiltrating credentials from cloud services.
Lesson to app developers: Time to discover the importance of two-factor authentication for everything you touch. You are targets.
